IRIS General description: Unterschied zwischen den Versionen
Lbanik (Diskussion | Beiträge) K (bilder auf eng) |
Lbanik (Diskussion | Beiträge) |
||
| Zeile 29: | Zeile 29: | ||
|- | |- | ||
|'''+''' Only minor change effort for existing systems | |'''+''' Only minor change effort for existing systems | ||
| − | |'''+''' Also accessible from [https:// | + | |'''+''' Also accessible from [https://en.wikipedia.org/wiki/Software_as_a_Service SaaS] ERP systems |
|- | |- | ||
|'''-''' Only possible with self-hosted (installed) ERP system | |'''-''' Only possible with self-hosted (installed) ERP system | ||
| − | [https:// | + | [https://en.wikipedia.org/wiki/Software_as_a_Service SaaS] based ERP systems are not possible. |
|'''+''' Developed according to the latest safety standards | |'''+''' Developed according to the latest safety standards | ||
|- | |- | ||
| Zeile 59: | Zeile 59: | ||
Authenticated: Each user is given a personal account in the IRIS system with which to log in. | Authenticated: Each user is given a personal account in the IRIS system with which to log in. | ||
| − | Authorized: Authorizations for functions in the dispatch system can be assigned for each user, according to the [https:// | + | Authorized: Authorizations for functions in the dispatch system can be assigned for each user, according to the [https://en.wikipedia.org/wiki/Role-based_access_control] |
| Zeile 81: | Zeile 81: | ||
Bitte planen Sie deshalb auch ein Gespräch mit Ihrem ERP-System-Hersteller, um diese Anforderungen zu besprechen. Hierzu zählen u.a.: | Bitte planen Sie deshalb auch ein Gespräch mit Ihrem ERP-System-Hersteller, um diese Anforderungen zu besprechen. Hierzu zählen u.a.: | ||
| − | * Only possible with our latest [https://interface.heidler-strichcode.de/ REST | + | * Only possible with our latest [https://interface.heidler-strichcode.de/ REST interface] |
* Requests only via an HTTPS connection | * Requests only via an HTTPS connection | ||
| − | * Authentifizierung mit [https:// | + | * Authentifizierung mit [https://en.wikipedia.org/wiki/OAuth OAuth2] (nur über die "Authorization Code" Methode) |
Version vom 16. Februar 2023, 16:59 Uhr
Issues with cloud systems
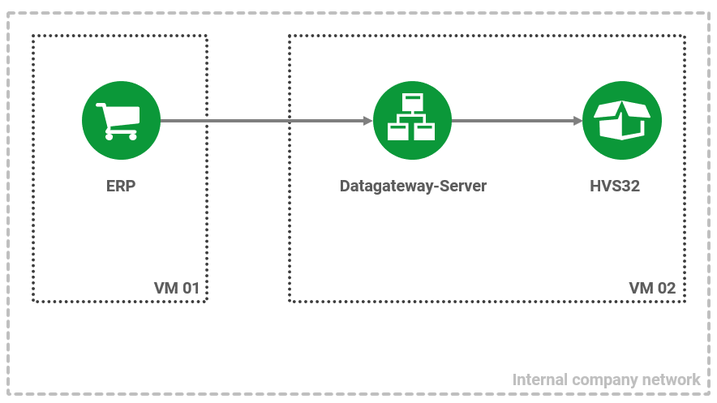
In principle, the HVS32 can be operated in cloud environments without hesitation, provided that the connection from the upstream system (ERP or WMS, hereinafter referred to as just ERP for simplicity) to the HVS32 is in a shared, secure, internal network.
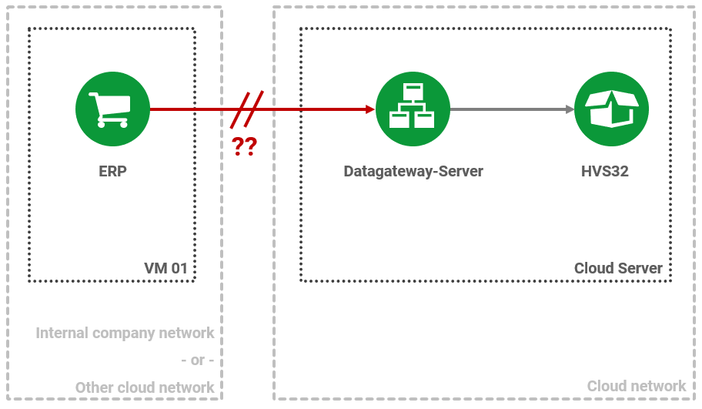
Problems arise, however, when a connection is to take place across networks:
Then this connection between two networks must be secured.
Secured means: Both the connection must be encrypted and each incoming connection must be authenticated and authorized.
There are two possibilities for this. The bridging of the networks by means of VPN or the secured publication of the HVS32 functions to the Internet with IRIS, a software developed by Heidler Strichcode.
VPN vs IRIS
There is no 100% perfect solution for securing the network bridge. Mostly you have to choose a compromise depending on the case.
Here we will list the common advantages and disadvantages of a VPN connection compared to IRIS to help you decide.
| VPN | IRIS |
|---|---|
| + Simple setup | + Accessible from the internet |
| + No further safety concerns | + Accessible for multiple ERP systems simultaneously |
| + Only minor change effort for existing systems | + Also accessible from SaaS ERP systems |
| - Only possible with self-hosted (installed) ERP system
SaaS based ERP systems are not possible. |
+ Developed according to the latest safety standards |
| - HVS32 is only accessible within these 2 networks
The VPN connection becomes mandatory for every client |
+ Future features possible, e.g. information in web interface (in planning) |
| - Difficult scalability
Multiple ERP systems only with extension of VPN connection |
- Complex setup of all security-related technologies |
| - Higher technical requirements for clients (ERP systems) | |
| - Regular (security) updates required |
IRIS in the cloud environment
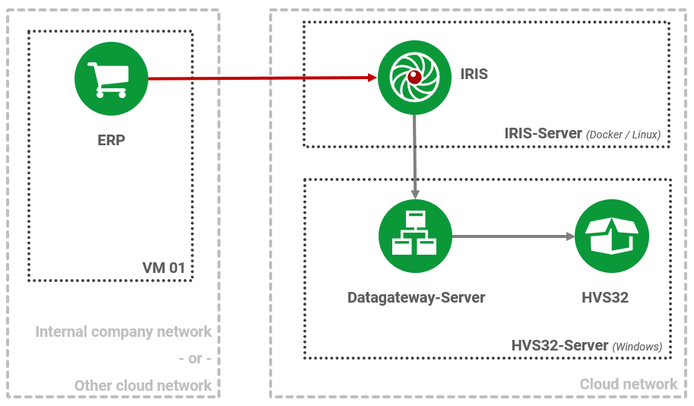
If you decided to use IRIS, the IRIS system would integrate with your internal corporate or cloud network as follows:
All requests to IRIS are encrypted, authenticated, and authorized.
Encrypted: Encryption is possible via HTTPS using TLSv1.2 or TLSv1.3 (if supported by the client).
Authenticated: Each user is given a personal account in the IRIS system with which to log in.
Authorized: Authorizations for functions in the dispatch system can be assigned for each user, according to the [1]
In addition, the IRIS system can manage multiple HVS32 systems simultaneously.
Example:
You use both a test and a production system. Using a simple identifier in the request to IRIS, the request is forwarded to the respective system.
You use different HVS32 installations for multiple sites. However: All HVS32 installations must then be located in the same internal company network.
Challenges
Every new software naturally comes with new challenges and requirements for the system.
We would like to point out at this point that the introduction of a security-relevant application such as IRIS can also bring with it various challenges and the security of the overall system must also be regularly checked from all sides.
We have described further details on the requirements for an installation on our IRIS Systemvoraussetzungen page.
In addition, however, these security requirements also make ERP system connectivity more complex. Additional challenges arise for the ERP system, which must also implement these requirements at least as a client of the shipping system. Bitte planen Sie deshalb auch ein Gespräch mit Ihrem ERP-System-Hersteller, um diese Anforderungen zu besprechen. Hierzu zählen u.a.:
- Only possible with our latest REST interface
- Requests only via an HTTPS connection
- Authentifizierung mit OAuth2 (nur über die "Authorization Code" Methode)